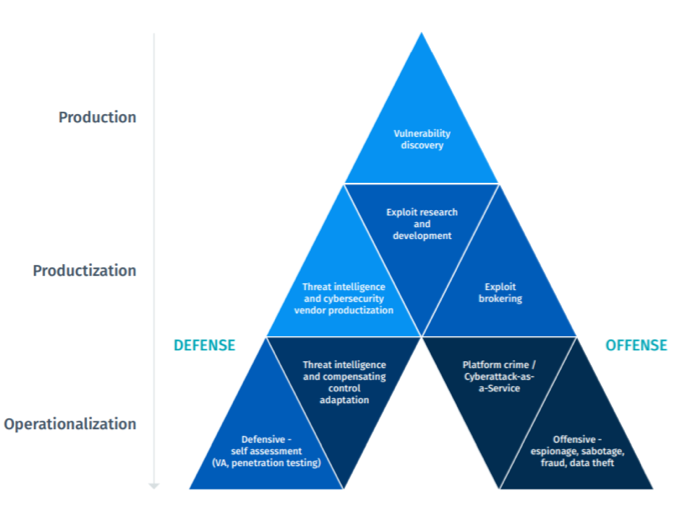
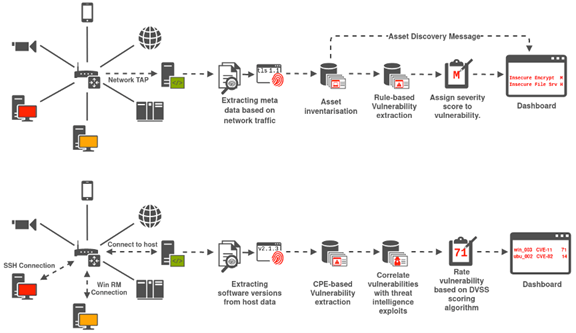
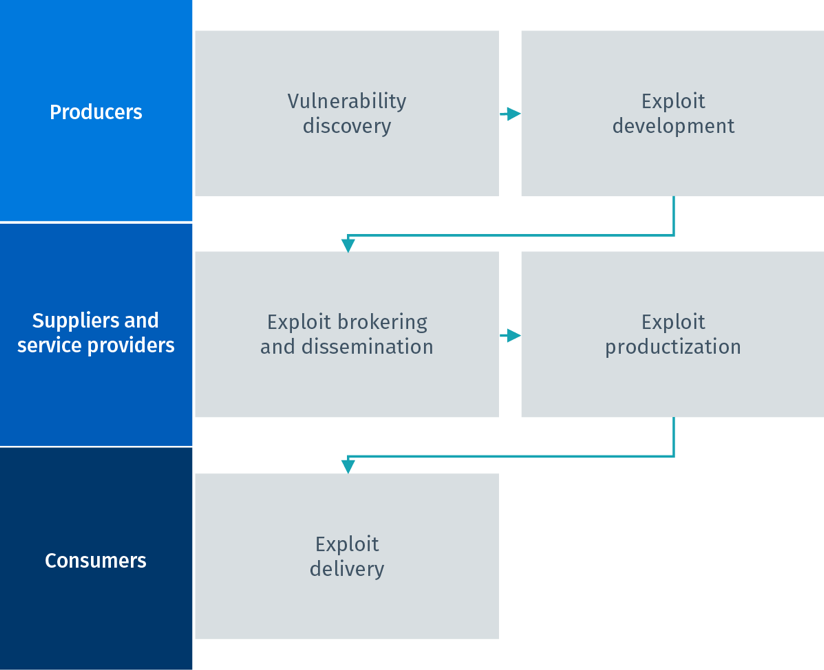
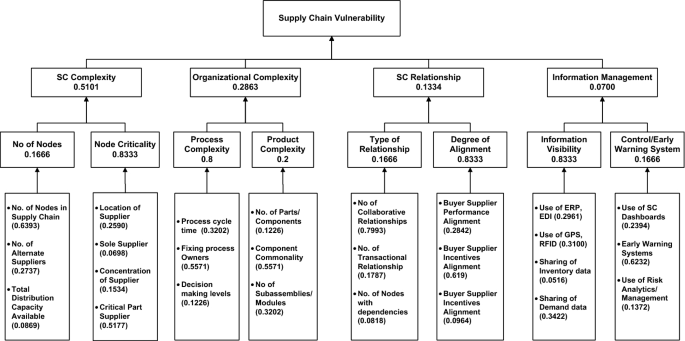
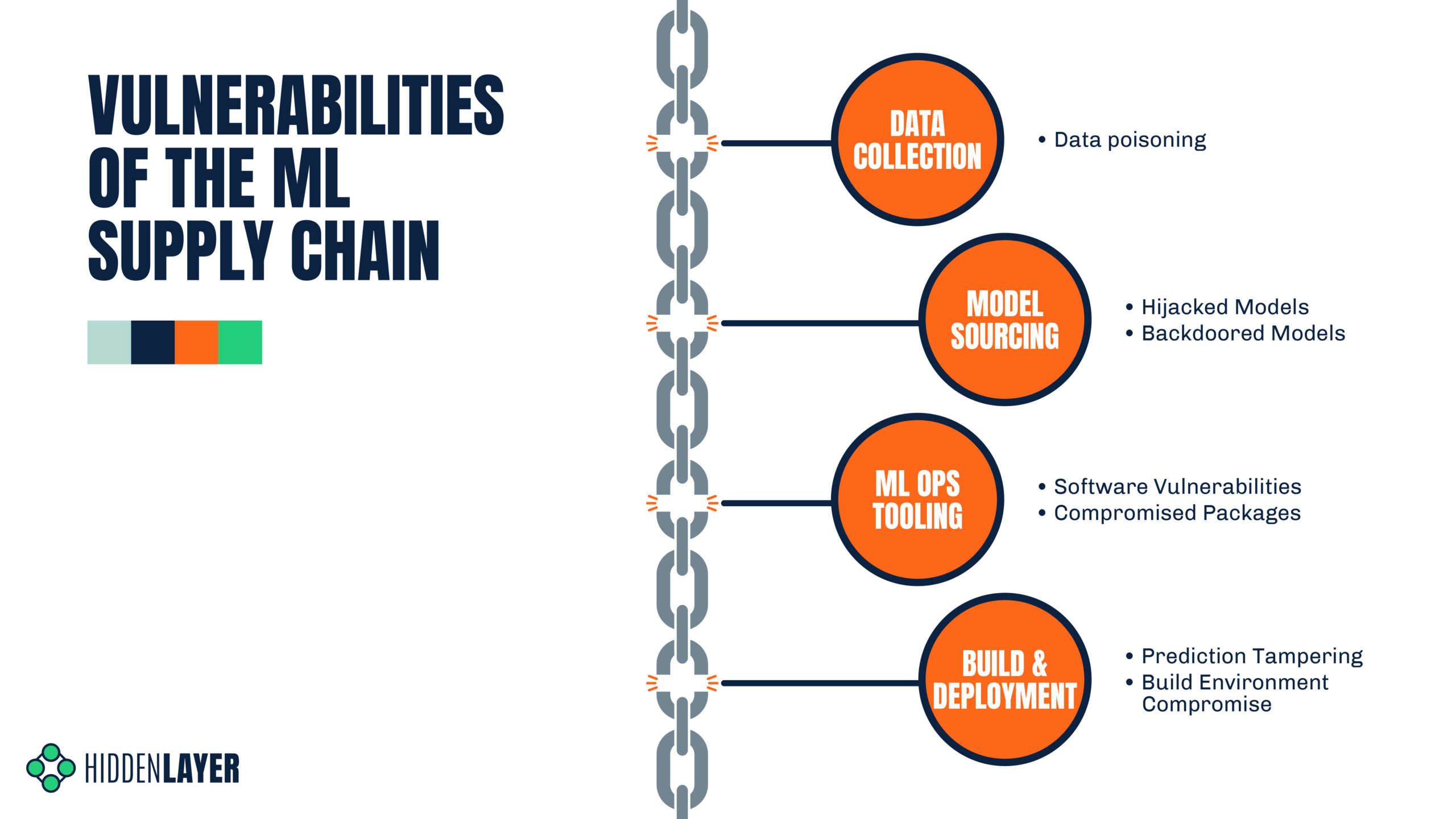
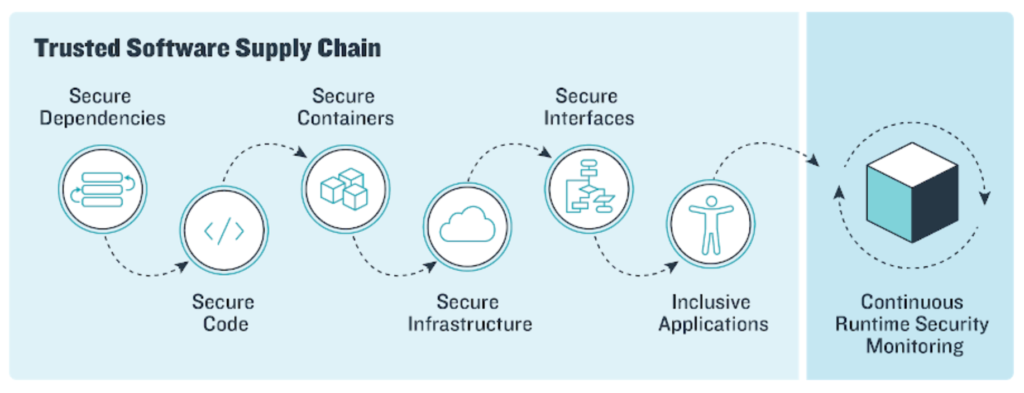
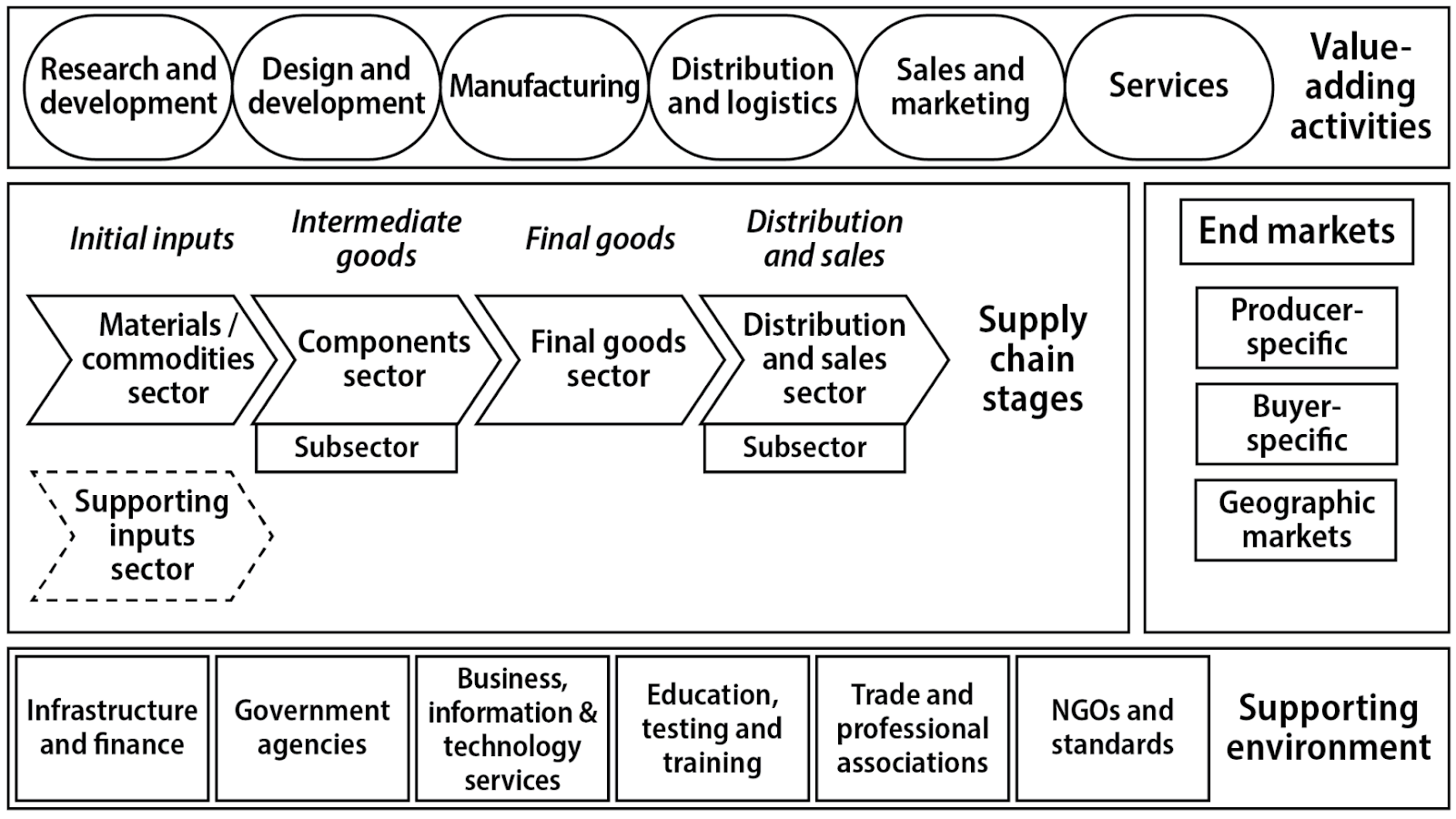
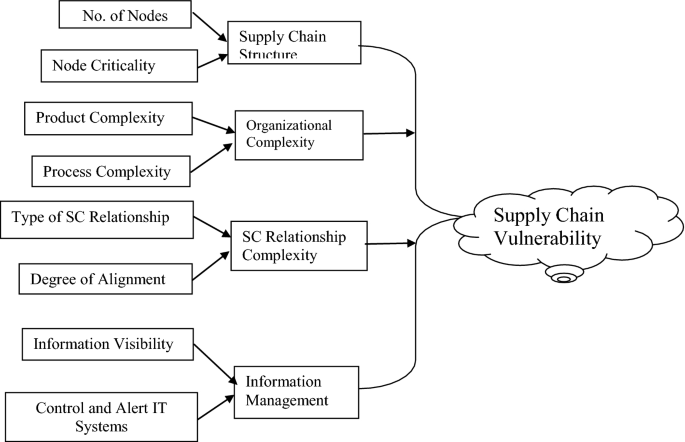
Supply chain vulnerability assessment: A network based visualization and clustering analysis approach - ScienceDirect
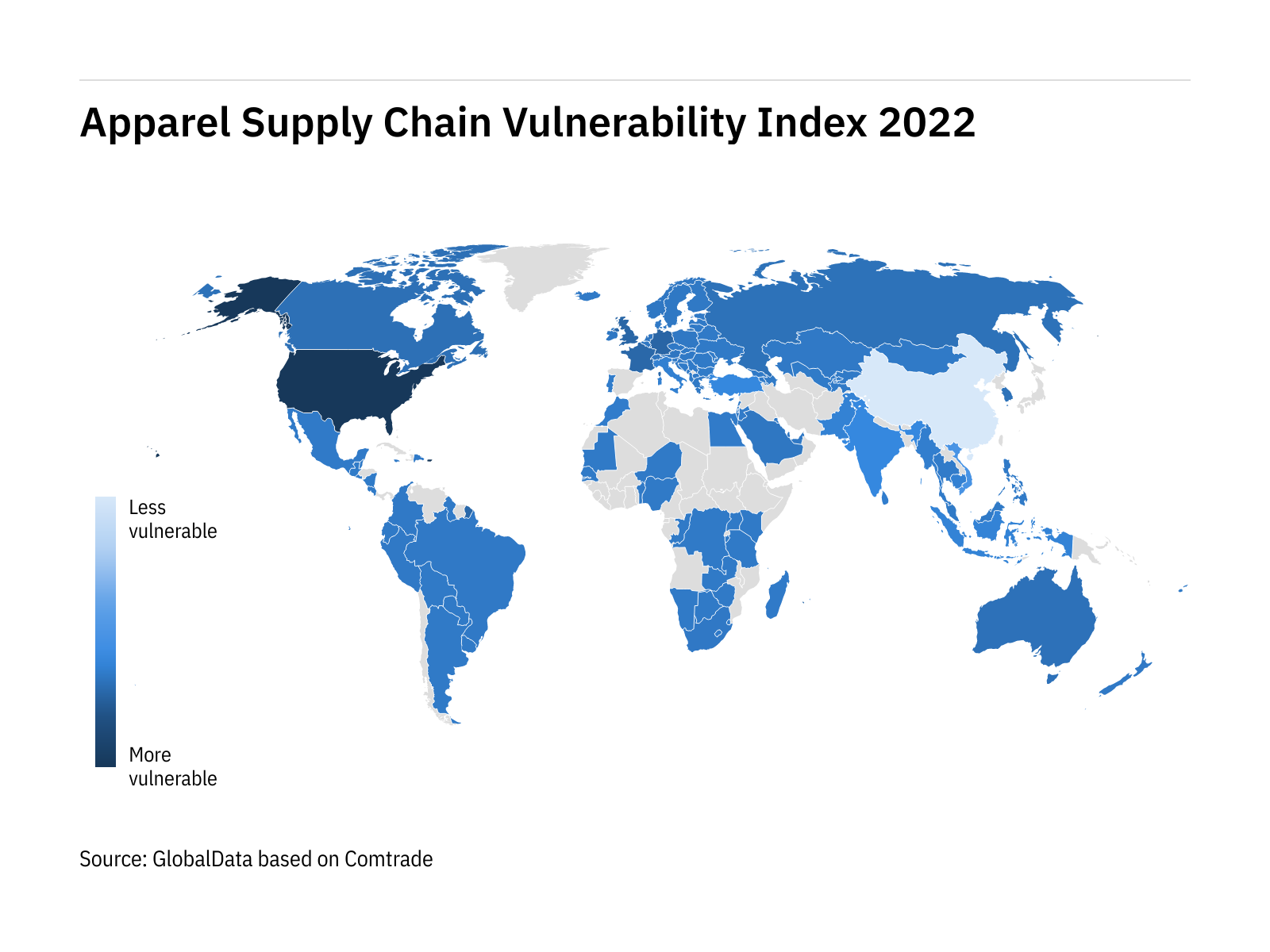
China's resilience shines through in index of world's most vulnerable apparel supply chains - Just Style

The Supply Chain Vulnerability Scan from Cosmo Tech is now Available on the SAP® Store | Business Wire

Amazon.com: Managing Supply Chain Risk and Vulnerability: Tools and Methods for Supply Chain Decision Makers: 9781848826335: Wu, Teresa, Blackhurst, Jennifer Vincent

Amazon.com: Supply Chain Risk Management: Vulnerability and Resilience in Logistics: 9780749463939: Waters, Donald